Projekt #SafeSecLab
 down
down
Motivation
Networked industrial networks need new IT security tools
Adaptive work systems require agile security concepts
Integrative security through safety and security by design
Research and Development...
... at the highest level, right on the pulse of industry
| 30+ faculty members | TU Wien and TÜV AUSTRIA experts |
| Inter-faculty research group | Computer science, electrical engineering & information technology, mechanical engineering & business administration, safety & security |
| 9 dissertation projects | Applied interdisciplinary research |
| Scientific Advisory Board | With leading personalities from industry and research |
| Industry-oriented development | In the pilot factory Industry 4.0 and other state of the art laboratories of TU Vienna and TÜV AUSTRIA |
| Transfer to industrial practice | Support from TÜV AUSTRIA experts, involvement of selected lead customers |
"Research priorities along the lifecycle of a cyber-physical production system"

Topics: Security architectures in the Industrial Internet of Things, threat modeling, hardware security by
Design, IT / OT convergence, ...

Topics: machine learning based attack detection, real-time intrusion detection for industrial control systems, automated security assessment procedures, ...

Topics: Security concepts using digital twin models, continuous integration and deployment, threat and risk analysis tools, ...
9 networked individual projects
P1: SafeSecLab Modeling
P2: SafeSecLab System Architecture
P3: Multi-Dimensional Intrusion Detection for Industrial Control Systems
P4: Safety-related design and simulation
P5: Automated Risk Management for Industrial Control Systems
P6: Model-based Security & Safetey Evaluation of OT Components
P7: Design-Time Hardware-Security Verification
P8: Safety-related assessment procedures for continuous integration and deployment
P9: Automated security assessment procedures for dynamically reconfigurable work systems
PhD 1
SafeSec System Modeling
Siegfried Hollerer
Supervisor: Wolfgang Kastner
Co-Supervisor: Thilo Sauter
TÜVA Contact person: Christoph Schwald
The PhD “SafeSecSystem Modeling” aims to identify approaches for modeling secure while safe system architectures in industrial environments. The resulting model shall fulfill requirements of both cyber security and functional safety.
Assets to be protected will be identified (e.g. critical devices, operators, production sites or plants) on a risk-based approach, since failure of a safety relevant device may have a more serious impact on the overall architecture than the failure of an HMI (Human Machine Interface).
Attack vectors and threats on assets will be discovered which also includes machine-to-machine communication and the integration of IT (Information Technology) and OT (Operational Technology). Figure 1 shows the mentioned convergence based on the international standard ISA 95.
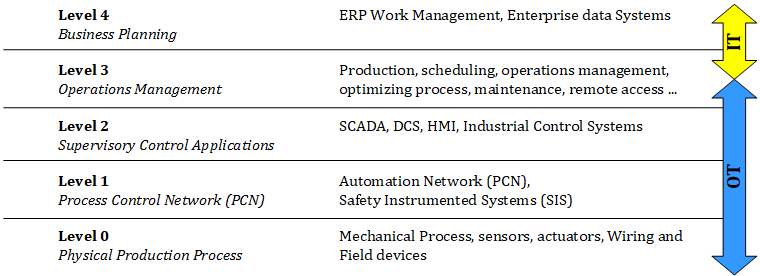
Figure 1: IT/OT integration model according to ISA 95 standard [1]
IT and OT have evolved differently which leads to challenges when merging both areas. IT focusses on security protection goals. Confidentiality and integrity are treated with priority where a temporary outage for some minutes has no severe impact in a typical IT architecture. On the contrary, in the OT domain loss of availability can lead to critical impacts that influence functional safety (e.g. The machine should enter a safe state once the light grid has been activated. Due to weak or missing security measures, the system gets manipulated and data of the light barrier cannot not be evaluated anymore. Thus, the safety function is deactivated and the machine continues to operate also in dangerous situations.).
Attack vectors can be based on organizational topics like phishing, security awareness trainings, handling of needed legacy systems, defining and enforcing security policies. Additionally, attacks can be related to technical topics like implementation of outdated or no encryption algorithms, the usage of services with weak security by design (e.g. the TCP protocol TFTP has no authentication implemented) or configuration issues of devices and their underlying services and applications.
To model the desired secure and safe architecture, classical IT threat modeling (e.g. STRIDE, Attack Trees) and safety related threat modeling are to be revised, adapted and combined with RAMI (Reference Architectural Model Industry 4.0).
Depending on the discovered threats, the resulting threat model will estimate the overall risk. Based on the identified threats, a catalogue of protection measures will be created to evaluate CPPS (Cyber Physical Production Systems) regarding safety and security. Furthermore, international standards (e.g. IEC 62443, IEC 61508) will be used to build the architecture model.
Reference
[1] ANSI/ISA 95.00.01-2000, Enterprise-Control System Integration Part 1: Models and Terminology, 2000, ISA
PhD 2
SafeSec System Architecture
Ali Hosseini
Supervisor: Thilo Sauter
Co-Supervisor: Wolfgang Kastner
TÜVA Contact person: Christoph Schwald
“Distributed automation systems and the associated Operational Technology (OT) have grown over the years and use a large number of communication technologies and Information Technology (IT). In conventional Automation Systems, safety and security were not valued as much as should be. The automation industry requires high performance, robustness, and real-time capability. The connection of the traditional OT to the current IT poses a potential threat to the real-time capability and may diminish the system performance. The major goal of this project is to generate safety and security integrated IT/OT architecture which enables a safe and secure integration of the different levels of the automation pyramid. The challenges that will be trying to be addressed are network security, hierarchical security architecture, security/safety versus real-time requirements, and challenges of limited resources in automation systems.”
PhD 3
Multi-Dimensional Intrusion Detection for Industrial Control Systems
Bernhard Brenner
Supervisor: Tanja Zseby
TÜVA Contact person: Thomas Doms
“State-of-the-art research shows evidence for the potential of anomaly-based intrusion detection in industrial control networks (ICSs). ICSs typically consist of a set-up that is well definable, with infrequent changes [1, 2] while the typically low data rates of ICS networks enable more complex data processing despite real-time constraints [3, 4].
Therefore, the aim of this project is to develop methods to detect attack preparations and ongoing attacks as well as their effects in ICS networks. Anomalies in network traffic shall be detected and, with the network-based detection, linked to other data sources (e.g., system information, environmental sensors, context information) to support security experts aligned with operations responsible staff in assessing the situation to ensure continuous safe and secure operations and data integrity/confidentiality.
Challenges here are:
- the different communication patterns of industrial networks (compared to IT networks)
- the extraction of suitable features for detection from network traffic
- the quality of the detection methods (that is, a high classification accuracy in practice)
- time and bandwith related constraints to classification
… in addition to the challenges of IDS avoidance techniques (such as packet fragmentation, covert channels) and the trend to encrypted network traffic as it can also be observed in IT networks [5].
We simulate attacks and IDS avoidance techniques in real ICS networks with the goal to obtain features to identify such attacks. Apart from finding suitable features for these kinds of attacks, we compare different types of classification techniques to find the best combination regarding computational effort and correctness. Figure 1 shows a brief depiction of our approach.
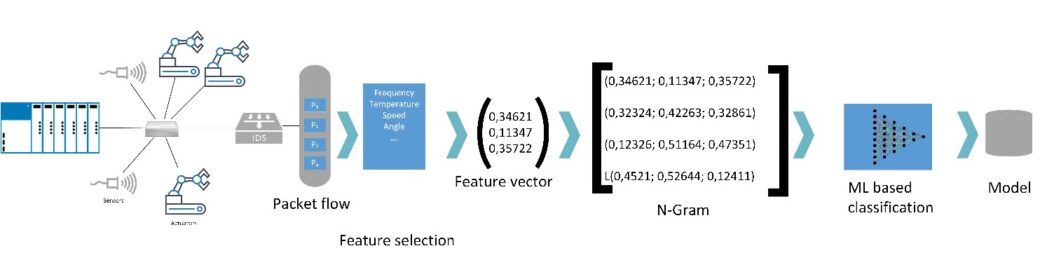
Figure 1: From raw network traffic to machine learning based traffic/attack classification.
As soon as these steps are accomplished, we develop a prototype based on elastic S²IEM for real-world factories. All insights gained during the work on this project will be published in topic-related, high rated conferences and journals.”
[1] M. Mantere, I. Uusitalo, M. Sailio, and S. Noponen, “Challenges of machine learning based monitoring for industrial control system networks,” in 2012 26th International Conference on Advanced Information Networking and Applications Workshops, 2012, pp. 968–972.
[2] R. Sommer and V. Paxson, “Outside the closed world: On using machine learning for network intrusion detection,” in 2010 IEEE symposium on security and privacy, 2010, pp. 305–316.
[3] R. R. Barbosa, R. Sadre, and A. Pras, “Difficulties in modeling SCADA traffic: a comparative analysis,” in International Conference on Passive and Active Network Measurement, 2012, pp. 126–135.
[4] F. Schuster, A. Paul, and H. König, “Towards learning normality for anomaly detection in industrial control networks,” in IFIP International Conference on Autonomous Infrastructure, Management and Security, 2013, pp. 61–72.
[5] Sandvine, Sandvine Global Internet Phenomena report 2018. URL: https://www.sandvine.com/hubfs/downloads/phenomena/2018-phenomena-report.pdf.
PhD 4
Safety-related design and simulation of cyber-physical-production-systems
Clara Fischer
Supervisor: Sebastian Schlund
TÜVA Contact person: Martin Steiner, Michael Neuhold
In this PhD topic methods for a computer-based, safety-oriented design based on simulations of cyber-physical-production-systems in discrete manufacturing and process industry are developed. In addition to the safety aspects, security risks will also be considered.
More preciesely, the following research questions should be answered within this project:
How can biomechanical limits and the resulting protection zones for cyber-physical systems be simulated or integrated into existing (process) simulations?”
Which can be devided into three subquestions:
- What are the requirements for fenceless cyberphysical work systems for safe collaboration, in direct interaction with humans?
- How can a collision with a cobot be represented in a model and how can biomechanical limit values be calculated or derived from it?
- To what extent is an automated safety assessment of an application, with a fence-less cyber-physical production system with direct interaction with humans, possible using process simulation software?
PhD4 is in close collaboration with PhD1, PhD2, PhD3, PhD5, PhD6 and PhD9.
PhD 5
Automated Risk Management for Industrial Control Systems
Pushparaj Bhosale
Supervisor: Wolfgang Kastner
Co-Supervisor: Thilo Sauter
TÜVA Contact person: Christoph Schwald
“Riskmanagement is an important insight which shapes the safety and security of an organization. The increasing threats in an everchanging industrial environment has made it difficult to meet the required safety and security standards in industrial control systems (ICS). This PhD to pic attempt stoachieve automated risk identification, analysis and assessment for information security in ICS. The project aims to find the state-of-the-art identification of security-relevant data and continuous collection of this data to obtain a useful model. Cost-effective risk reduction techniques are to be implemented and validated.”
PhD 6
Model-based Security & Safetey Evaluation of OT Components
Mukund Bhole
Supervisor: Wolfgang Kastner
Co-Supervisor: Thilo Sauter
TÜVA Contact person: Thomas Doms
“The aim of this PhD is to develop methods for testing of security and safety features of OT components on the basis of engineering artifacts – in particular their specification.
- Are all specified requirements (e.g., secure protocols and authentication procedures, patch levels, configurations) met?
- Can any weak points (e.g., concerning automated tests) be identified?
The results of the tests will be assessed both qualitatively and quantitatively with regard to their potential effects. Methods are invesitage to automatically identify and evaluate countermeasures.”
PhD 7
Design-Time Hardware-Security Verification
Sofia Maragkou
Supervisor: Axel Jantsch
TÜVA Contact person: Christoph Schwald
“In the concept of Computer Systems security, it is largely assumed that the underlying hardware is trusted. In “Cyber-Physical Systems “(CPS) security implications can have direct impact on functional safety and thus it can put human lives in danger. Taking into consideration this fact and the new age of Industry 4.0, the case study is formed based on the given context.
The main purpose of this project is the development of a method which will detect malicious hardware using application specific framework conditions. The final result will be a workable software tool that will demonstrate the effectiveness of this method.
In contrast to the existing ones, this method enables the elimination of security gaps, as well as the formulation of security policies for hardware designs. This makes our method more flexible regarding unknown attacks, since it can be used as required and it can be expanded in order to include appropriate policies.
During the research for this project, some interesting questions will be answered. For example how can unauthorized information flow be recognised during design-time, if we can leverage pattern graph specifications to specify information flow policies and how can we verify the correctness of information flow authorization.
At first, the investigation of state-of-the-art M2M hardware authentication and state-of-the-art communication options for hardware Trojans have to take place. Another factor that should be taken into consideration is the factor of the threat models that can be considered possible in the given context. Having those factors well oriented, the authentication of hardware in the given threat models and be specified.
Consequently the detection tool can be prototyped. After the verification of the benchmarks the tool can be validated. Based on the research done at the previous parts mentioned above, a catalog of the countermeasures can be drafted.
An important outcome of this project will be the determination of the security requirements for a machine-to-machine (M2M) communication controller because of the hazards that can occur. For example, part of the security problems which are created by M2M communication is the key generation and distribution. In case an adversary/attacker extracts the secret key of an existing communication channel of IoT devices, they can take complete control of the digital factory.”
PhD 8
Safety-related assessment procedures for continuous integration and deployment
Bernd Hader
Supervisor: Sebastian Schlund
Co-Supervisor: Wolfgang Kastner
TÜVA Contact person: Thomas Doms
Due to the increasing convergence of IT and OT in the industrial sector, short-cycle software delivery, also called Continuous Delivery (CD), is also gaining importance in manufacturing. There are essentially two reasons for this. On the one hand, updates are necessary to adapt the networked devices and systems to the technological progress, to provide new functionalities and to remain competitive. On the other hand, these updates are also necessary to fix errors and especially potential security flaws within the software as quickly as possible. Due to these requirements of rapid software delivery, an approach called DevOps has evolved in agile software development. The goal of DevOps is to deliver good quality software as quickly as possible; this is achieved through direct collaboration between the two areas of Development and Operations and by automating as many parts of this process as possible.
Current developments in manufacturing and the use of collaborative robots (cobots) are gradually blurring the boundaries between man and machine, and humans and robots are working together without a protective fence. Ensuring personal safety remains particularly important here. In this respect, the boundaries between safety and security are blurred in concrete applications and conceptual approaches of both areas should be considered in an integrated manner.
This project is dedicated to the question of what effects the short-cycle software updates have on the direct interaction between man and machine and how it can be ensured that personal safety is guaranteed at all times. In the course of this, a prototype will also be developed that will provide the risk assessment and corresponding measures to ensure safe operation during short-cycle software updates in production.
PhD 9
Automated security assessment procedures for dynamically reconfigurable work systems
Start 01.01.2021
Maximillian Papa
Supervisor: Sebastian Schlund
TÜVA Contact person: Martin Steiner, Michael Neuhold
Safety assessment procedures for fenceless work systems in direct human-machine interaction currently exhibit two major weaknesses that complicate and prolong the certification process. On the one hand, every time the system is reconfigured (change of the application or the entire “machine”, i.e. also of grippers, workpiece, code, layout or work cycle), the complete certification must be re-certified and, if necessary, the protective measures must be redesigned. On the other hand, current safety assessment procedures mainly consider risks of functional safety and neglect the corresponding security hazards. Both mentioned points have to be solved in order to carry out certification faster and more cost-effectively.
In addition to the other projects of the #SafeSecLab, the procedure to be developed in this specific project focuses primarily on the solution of these problems in automated safety assessments for dynamically reconfigurable work systems.
