Projekt #SafeSecLab
 down
down
Motivation
Vernetzte Industrienetzwerke brauchen neue IT-Security Werkzeuge
Adaptive Arbeitssysteme fordern agile Sicherheitskonzepte
Integrative Sicherheit über Safety und Security by Design
Forschung und Entwicklung...
...auf höchstem Niveau direkt am Puls der Industrie
| 30+ Faculty members | TU Wien und TÜV AUSTRIA Expertinnen und Experten |
| Interfakultäre Forschungsgruppe | Informatik, Elektrotechnik & Informationstechnik, Maschinenwesen & Betriebswissenschaften, Safety & Security |
| 9 Dissertationsprojekte | Angewandte interdisziplinäre Forschung |
| Scientific Advisory Board | Mit führenden Persönlichkeiten aus Industrie und Forschung |
| Industrienahe Entwicklung | In der Pilotfabrik Industrie 4.0 und weiteren State of the Art Laboren von TU Wien und TÜV AUSTRIA |
| Transfer in die industrielle Praxis | Begleitung durch TÜV AUSTRIA Expertinnen und Experten, Einbindung ausgewählter Lead-Kunden |
"Forschungsschwerpunkte entlang des Lifecycles eines Cyber-physischen Produktionssystems"

Topics: Sicherheitsarchitekturen im Industrial Internet of Things, Bedrohungsmodellierungen, Hardware Security by Design, IT/OT Konvergenz,…

Topics: Machine Learning basierte Angriffserkennung, Real-Time Intrusion Detection für industrielle Kontrollsysteme, automatisierte Sicherheitsbewertungsverfahren, …

Topics: Sicherheitskonzepte über Digital Twin Modelle, Continous Integration and Deployment, Threat and Risk Analysis Tools, …
9 vernetzte Einzelprojekte
P1: SafeSecLab Modeling
P2: SafeSecLab System Architecture
P3: Multi-Dimensional Intrusion Detection for Industrial Control Systems
P4: Sicherheitsgerichtetes Design und Simulation
P5: Automated Risk Management for Industrial Control Systems
P6: Model-based Security & Safetey Evaluation of OT Components
P7: Design-Time Hardware-Security Verification
P8: Sicherheitsgerichtete Bewertungsverfahren für Continous Integration and Deployment
P9: Automatisierte Sicherungsbewertungsverfahren für dynamisch rekonfigurierbare Arbeitssysteme
PhD 1
SafeSec System Modeling
Siegfried Hollerer
Poster
Betreuer: Wolfgang Kastner
Co-Betreuer: Thilo Sauter
TÜVA Ansprechperson: Christoph Schwald
Das Ziel des Dissertationsvorhabens „SafeSecSystem Modeling“ ist die Identifizierung von Vorgehensweisen, um sichere System-Architekturen im industriellen Umfeld zu modellieren. Das resultierende Modell soll sowohl Anforderungen der Cyber-Sicherheit, als auch der funktionalen Sicherheit erfüllen.
Zu schützende Assets (z.B.: kritische Geräte, Operatoren bzw. Bediener, Produktionsanlagen)
werden durch einen risikobasierten Ansatz identifiziert, da der Ausfall eines sicherheitskritischen
Gerätes einen höheren Schaden, als der Ausfall eines HMI (Human Machine Interface) in der
gesamten Architektur verursachen kann.
Es werden Angriffsvektoren und Bedrohungen der Assets identifiziert, welche die Kommunikation
zwischen Maschinen (Machine-to-Machine Communication) und die Integration von IT (Information
Technology) mit OT (Operational Technology) berücksichtigt. Abbildung 1 zeigt die erwähnte
Konvergenz auf Basis des Standards ISA 95.
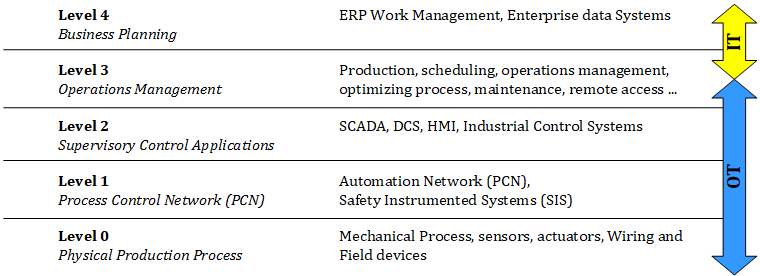
Abbildung 1: IT/OT – Integrationsmodell laut des Standards ISA 95 [1]
IT und OT haben sich unterschiedlich entwickelt, wodurch Herausforderungen bei der
Verschmelzung beider Gebiete entstehen. Die IT fokussiert sich auf Schutzziele hinsichtlich der
Cyber-Security. Vertraulichkeit und Integrität werden priorisiert behandelt, da ein temporärer
Ausfall eines Geräts oder Dienstes von einigen Minuten keinen erheblichen Schaden in einer
typischen IT-Architektur verursacht. Im Gegensatz dazu kann in einer OT-Architektur der Verlust der
Verfügbarkeit kritischen Schaden verursachen, welcher die funktionale Sicherheit beeinflusst.
Ein schwaches IT-Sicherheitsniveau kann die funktionale Sicherheit beinträchtigen, wie folgendes
Beispiel verdeutlicht: Eine Maschine soll in einen sicheren Zustand wechseln, sobald ein Lichtgitter
aktiviert wurde. Wegen schwachen oder fehlenden IT-Sicherheitsmaßnahmen konnte das System
manipuliert werden und die Daten des Lichtgitters können nicht mehr ausgewertet werden. Folglich
wurde die funktionale Sicherheitsfunktion deaktiviert und die Maschine führt ihren Betrieb auch in
einer gefährlichen Situation fort.
Angriffsvektoren können sich auf organisatorische Themen, wie Phishing, IT-Security Awareness-
Schulungen, den Umgang mit veralteten Systemen (Legacy-Systeme) oder die Definition und
Durchsetzung von IT-Security Richtlinien, beziehen. Zusätzlich können sich Angriffe auf technische
Themen beziehen, wie die Implementierung eines veralteten oder gar keinen
Verschlüsselungsalgorithmus, Schwächen in der Konfiguration von Geräten und deren Diensten und
Applikationen oder die Verwendung von Diensten mit schwacher IT-Security-Unterstützung (z.B.:
Das TCP-Protokoll TFTP hat keine Authentifizierung implementiert.).
Um die gewünschte sichere Architektur zu modellieren, werden klassische IT-Bedrohungsmodelle (z.B.: STRIDE, Attack Trees) und Bedrohungsmodelle, welche für die funktionale Sicherheit relevant sind, überarbeitet, adaptiert und kombiniert mit RAMI (Reference Architectural Model Industry 4.0).
Abhängig von den entdeckten Bedrohungen entsteht ein Bedrohungsmodell, welches das Gesamtrisiko abschätzt. Basierend auf den identifizierten Bedrohungen wird ein Katalog mit Schutzmaßnahmen erstellt, welcher das vorhandene Niveau der Cyber-Sicherheit und der funktionalen Sicherheit für CPPS (Cyber Physical Production Systems) evaluiert. Es werden internationale Standards (zB.: IEC 62443, IEC 61508) verwendet, um das Architektur-Modell zu erstellen.
Referenzen
[1] ANSI/ISA 95.00.01-2000, Enterprise-Control System Integration Part 1: Models and Terminology, 2000, ISA
PhD 2
SafeSec System Architecture
Ali Hosseini
Poster
Betreuer: Thilo Sauter
Co-Betreuer: Wolfgang Kastner
TÜVA Ansprechperson: Christoph Schwald
„Distributed automation systems and the associated Operational Technology (OT) have grown over the years and use a large number of communication technologies and Information Technology (IT). In conventional Automation Systems, safety and security were not valued as much as should be. The automation industry requires high performance, robustness, and real-time capability. The connection of the traditional OT to the current IT poses a potential threat to the real-time capability and may diminish the system performance. The major goal of this project is to generate safety and security integrated IT/OT architecture which enables a safe and secure integration of the different levels of the automation pyramid. The challenges that will be trying to be addressed are network security, hierarchical security architecture, security/safety versus real-time requirements, and challenges of limited resources in automation systems.“
PhD 3
Multi-Dimensional Intrusion Detection for Industrial Control Systems
Bernhard Brenner
Poster
Betreuer: Tanja Zseby
TÜVA Ansprechpartner: Thomas Doms
Der aktuelle Stand der Forschung zeigt das Potenzial von Anomalie-basierten Intrusion Detection Systemen (IDS) in industriellen Kontrollnetzwerken (ICS).
ICS bestehen typischerweise aus einem gut definierbaren Aufbau, welcher sich nur selten ändert [1, 2], während die relativ niedrigen Datenraten von ICS-Netzwerken in vielen Fällen eine komplexere Datenverarbeitung trotz Echtzeitbeschränkungen ermöglichen [3, 4].
Ziel dieses Projektes ist es nun, Methoden zur Erkennung von Angriffsvorbereitungen und laufenden Angriffen sowie deren Auswirkungen in ICS-Netzwerken zu entwickeln. Anomalien im Netzwerkverkehr sollen erkannt- und mit der netzwerkbasierten Erkennung mit anderen Datenquellen (z. B. Systeminformationen, Umgebungssensoren, Kontextinformationen) verknüpft werden, um Sicherheitsexperten in Zusammenarbeit mit Betriebsverantwortlichen bei der Beurteilung der Situation zu unterstützen und dadurch einen kontinuierlichen, sicheren Betrieb und die Datenintegrität/Vertraulichkeit zu gewährleisten.
Herausforderungen sind hier:
- die sich von IT Netzwerken unterscheidenden Kommunikationsmuster in industriellen Netzwerken
- die Extraktion von geeigneten Merkmalen („Features“) zur Erkennung von verdächtigem Netzwerkverkehr
- die Qualität der Erkennungsmethoden (d. h. eine hohe Klassifizierungsgenauigkeit im praktischen Einsatz)
- Zeit- und Bandbreiten-bedingte Einschränkungen bei der Klassifizierung
… zusätzlich zu den Herausforderungen der verfügbaren IDS-Umgehungstechniken (wie Paketfragmentierung, Covert Channels, etc.) und dem Trend zur verschlüsselten Kommunikation, wie er auch in IT-Netzwerken zu beobachten ist [5].
Wir simulieren Angriffe und IDS-Umgehungstechniken in realen ICS-Netzwerken mit dem Ziel, Merkmale zur Identifizierung solcher Angriffe zu erhalten. Neben der Suche nach geeigneten Merkmalen für diese Art von Angriffen vergleichen wir verschiedene Arten von Klassifizierungsverfahren, um die beste Kombination hinsichtlich Rechenaufwand und Korrektheit zu finden. Abbildung 1 zeigt eine kurze Darstellung unseres Ansatzes.
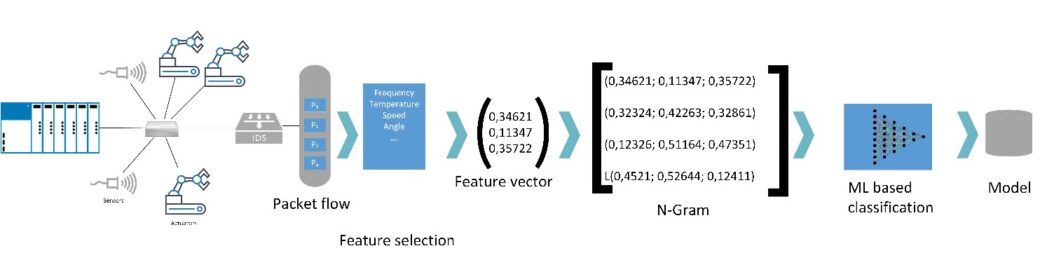
Abbildung 1: Vom Netzwerkverkehr zur auf maschinellem Lernen basierenden Klassifizierung des Netzwerkverkehrs.
Sobald diese Schritte abgeschlossen sind, entwickeln wir einen Prototyp auf Basis eines Elastic Stacks (Elastic S²IEM) für reale Fabriken. Alle Erkenntnisse, die während der Arbeit an diesem Projekt gewonnen werden, werden in themenbezogenen Konferenzen und Fachzeitschriften veröffentlicht.“
[1] M. Mantere, I. Uusitalo, M. Sailio, and S. Noponen, “Challenges of machine learning based monitoring for industrial control system networks,” in 2012 26th International Conference on Advanced Information Networking and Applications Workshops, 2012, pp. 968–972.
[2] R. Sommer and V. Paxson, “Outside the closed world: On using machine learning for network intrusion detection,” in 2010 IEEE symposium on security and privacy, 2010, pp. 305–316.
[3] R. R. Barbosa, R. Sadre, and A. Pras, “Difficulties in modeling SCADA traffic: a comparative analysis,” in International Conference on Passive and Active Network Measurement, 2012, pp. 126–135.
[4] F. Schuster, A. Paul, and H. König, “Towards learning normality for anomaly detection in industrial control networks,” in IFIP International Conference on Autonomous Infrastructure, Management and Security, 2013, pp. 61–72.
[5] Sandvine, Sandvine Global Internet Phenomena report 2018. URL: https://www.sandvine.com/hubfs/downloads/phenomena/2018-phenomena-report.pdf.
PhD 4
Sicherheitsgerichtetes Design und Simulation von cyberphysischen Arbeitssystemen
Clara Fischer
Poster
Betreuer: Sebastian Schlund
TÜVA Ansprechpartner: Martin Steiner, Michael Neuhold
Im Rahmen dieses Promotionsthemas werden Methoden für ein rechnergestütztes, sicherheitsgerichtetes Design auf der Grundlage von Simulationen cyberphysischer Arbeitssysteme, in der diskreten Fertigung und Prozessindustrie, entwickelt. Neben Safety- Aspekten werden auch die Risiken aus dem Bereich Datensicherheit (Security) mitbetrachtet.
Konkreter gesagt sollen in diesem Projekt die folgende Forschungsfragen beantwortet werden:
Wie können biomechanische Grenzwerte und die daraus resultierenden Schutzzonen für cyberphysische Arbeitssysteme simuliert bzw. in bestehende (Prozess-)Simulationen integriert werden?
Beziehungsweiße die Unterfragen:
- Welche Anforderungen haben schutzzaunlose cyberphysische Arbeitssysteme für eine sichere Zusammenarbeit, in direkter Interaktion mit dem Menschen zu erfüllen?
- Wie kann eine Kollision mit einem Cobot in einer Modellierung dargestellt werden und wie können daraus biomechanische Grenzwerte berechnet, beziehungsweise abgeleitet werden?
- Inwiefern ist eine automatisierte Sicherheitsbewertung einer Anwendung, mit einem schutzzaunlosen cyberphysichen Produktionssystem mit direkter Interaktion mit dem Menschen, mit Hilfe einer Prozesssimulationssoftware möglich?
PhD 4 steht im engen Austausch mit PhD1, PhD2, PhD3, PhD5, PhD6 und PhD9.
PhD 5
Automated Risk Management for Industrial Control Systems
Pushparaj Bhosale
Poster
Betreuer: Wolfgang Kastner
Co-Betreuer: Thilo Sauter
TÜVA Ansprechperson: Christoph Schwald
„Riskmanagement is an important insight which shapes the safety and security of an organization. The increasing threats in an everchanging industrial environment has made it difficult to meet the required safety and security standards in industrial control systems (ICS). This PhD to pic attempt stoachieve automated risk identification, analysis and assessment for information security in ICS. The project aims to find the state-of-the-art identification of security-relevant data and continuous collection of this data to obtain a useful model. Cost-effective risk reduction techniques are to be implemented and validated.“
PhD 6
Model-based Security & Safetey Evaluation of OT Components
Mukund Bhole
Poster
Betreuer: Wolfgang Kastner
Co-Betreuer: Thilo Sauter
TÜVA Ansprechperson: Thomas Doms
„The aim of this PhD is to develop methods for testing of security and safety features of OT components on the basis of engineering artifacts – in particular their specification.
- Are all specified requirements (e.g., secure protocols and authentication procedures, patch levels, configurations) met?
- Can any weak points (e.g., concerning automated tests) be identified?
The results of the tests will be assessed both qualitatively and quantitatively with regard to their potential effects. Methods are invesitage to automatically identify and evaluate countermeasures.“
PhD 7
Design-Time Hardware-Security Verification
Sofia Maragkou
Poster
Betreuer: Axel Jantsch
TÜVA Ansprechperson: Christoph Schwald
„In the concept of Computer Systems security, it is largely assumed that the underlying hardware is trusted. In “Cyber-Physical Systems “(CPS) security implications can have direct impact on functional safety and thus it can put human lives in danger. Taking into consideration this fact and the new age of Industry 4.0, the case study is formed based on the given context.
The main purpose of this project is the development of a method which will detect malicious hardware using application specific framework conditions. The final result will be a workable software tool that will demonstrate the effectiveness of this method.
In contrast to the existing ones, this method enables the elimination of security gaps, as well as the formulation of security policies for hardware designs. This makes our method more flexible regarding unknown attacks, since it can be used as required and it can be expanded in order to include appropriate policies.
During the research for this project, some interesting questions will be answered. For example how can unauthorized information flow be recognised during design-time, if we can leverage pattern graph specifications to specify information flow policies and how can we verify the correctness of information flow authorization.
At first, the investigation of state-of-the-art M2M hardware authentication and state-of-the-art communication options for hardware Trojans have to take place. Another factor that should be taken into consideration is the factor of the threat models that can be considered possible in the given context. Having those factors well oriented, the authentication of hardware in the given threat models and be specified.
Consequently the detection tool can be prototyped. After the verification of the benchmarks the tool can be validated. Based on the research done at the previous parts mentioned above, a catalog of the countermeasures can be drafted.
An important outcome of this project will be the determination of the security requirements for a machine-to-machine (M2M) communication controller because of the hazards that can occur. For example, part of the security problems which are created by M2M communication is the key generation and distribution. In case an adversary/attacker extracts the secret key of an existing communication channel of IoT devices, they can take complete control of the digital factory.“
PhD 8
Sicherheitsgerichtete Bewertungsverfahren für Continous Integration and Deployment
Bernd Hader
Poster
Betreuer: Sebastian Schlund
Co-Betreuer: Wolfgang Kastner
TÜVA Ansprechperson: Thomas Doms
Durch die zunehmende Konvergenz von IT und OT im industriellen Sektor gewinnt auch in der Produktion die kurzzyklische Softwareauslieferung an Bedeutung. Hierfür gibt es im Wesentlichen zwei Gründe. Einerseits sind Updates notwendig, um die vernetzten Geräte und Anlagen an den technologischen Fortschritt anzupassen, neue Funktionalitäten bereitzustellen und wettbewerbsfähig zu bleiben. Andererseits sind diese Updates aber auch erforderlich, um Fehler und insbesondere potenzielle Sicherheitslücken innerhalb der Software schnellstmöglich zu beheben. Durch diese Anforderungen der schnellen Softwareauslieferung hat sich in der agilen Softwareentwicklung ein Ansatz, namens DevOps, entwickelt. Das Ziel von DevOps ist es Software in guter Qualität möglichst rasch auszuliefern, umgesetzt wird dies durch die direkte Zusammenarbeit der beiden Bereiche Development (zuständig für die Softwareentwicklung) und Operations (zuständig für den IT-Betrieb) sowie durch die Automatisierung möglichst vieler Teile dieses Prozesses.
Durch die aktuellen Entwicklungen in der Produktion und den Einsatz von kollaborativen Robotern (Cobots) verschwimmen allmählich die Grenzen zwischen Mensch und Maschine und Mensch und Roboter arbeiten gemeinsam und schutzzaunlos zusammen. Besonders wichtig hierbei bleibt die Gewährleistung der Personensicherheit. Insofern verschwimmen hierbei in der konkreten Anwendung die Grenzen zwischen Personensicherheit (Safety) und Informationssicherheit (Security) bzw. sollten konzeptuelle Ansätze beider Bereiche integriert betrachtet werden.
Dieses Projekt widmet sich der Frage, welche Auswirkungen die kurzzyklischen Softwareupdates auf die direkte Interaktion von Mensch und Maschine haben und wie gewährleistet werden kann, dass die Personensicherheit zu jedem Zeitpunkt sichergestellt ist. Im Zuge dessen soll auch ein Prototyp entwickelt werden, welcher die Risikobewertung und dementsprechend Maßnahmen bereitstellt, um den sicheren Betrieb bei der kurzzyklischen Softwareaktualisierung zu gewährleisten.
PhD 9
Automatisierte Sicherungsbewertungsverfahren für dynamisch rekonfigurierbare Arbeitssysteme
Maximillian Papa
Poster
Betreuer: Sebastian Schlund
TÜVA Ansprechperson: Martin Steiner, Michael Neuhold
Sicherheitsbewertungsverfahren für schutzzaunlose Arbeitssysteme in direkter Mensch-Maschine-Interaktion weisen heute zwei wesentliche Schwächen auf, die einen Zertifizierungsprozess erschweren und verlängert. Zum einen muss bei jeder Rekonfiguration des Systems (Veränderung der Applikation bzw. der gesamten „Maschine“, d.h. auch von Greifer, Werkstück, Code, Layout oder Arbeitstakt die komplette Zertifizierung neu und ggf. auch die Schutzmaßnahmen neugestaltet werden. Zudem berücksichtigen die Sicherheitsbewertungsverfahren heute vor allem Risiken der funktionalen Sicherheit (Safety) und vernachlässigen zusammenhängende IT-Sicherheitsgefahren (Security). Beide Fragen müssen gelöst werden, um eine Zertifizierung schneller und günstiger durchzuführen.
In Ergänzung zu den andere Projekten des #SafeSecLab, konzentriert sich das in diesem spezifischen Projekt zu entwickelnde Verfahren vor allem auf die Lösung dieser Probleme bei automatisierten Sicherheitsbewertungen für dynamisch rekonfigurierbare Arbeitssysteme.
